✨ An opensource project to create a docker image of XMRig miner and mining cryptocurrencies using containers ✨
Getting Started | Usage | Concepts | Security | Versioning
If you want contribute on this project, first you need to make a git clone:
- git clone --depth 1 https://github.com/lpmatos/docker-crypto-miner.git -b main
This will give you access to the code on your local machine.
This tool is for educational and ethical practices only. The developers are not responsible if the tool is misused by an individual. Use at your own risk. If you plan to mine on a cloud check the terms and conditions before you start. The same applies if you are using private equipment or an on-site datacenter for mining.
This repository contains a setup with Docker that let you get from zero to mining in around 5 minutes on any Linux host anywhere. CPU mining can be profitable using algorithmns like: RandomX, Cryptonight, or Equihash. Find out more about profitability here.
docker pull ghcr.io/lpmatos/docker-crypto-miner:mainThe preferred way to configure XMRig is using a configuration file in JSON format because it is more flexible and user-friendly. CLI does not cover all features available and can be a limiting factor depending on the scenario.
| Environment | Description |
|---|---|
| MINING_POOL | URL of mining server |
| MINING_COIN | Coin to mining |
| REFERRAL_CODE | Param to educe mining rater |
| WALLET_ADDRESS | Wallet address |
| WORKER_NAME | Worker name |
| XMRIG_CONFIG_FILE | XMRig config file reference |
To run the docker container:
docker container run \
--restart unless-stopped --name crypto-miner -d \
-e MINING_POOL="rx.unmineable.com:3333" \
-e MINING_COIN="SHIB" \
-e REFERRAL_CODE="7lkr-kmhq" \
-e WALLET_ADDRESS="<your-wallet-address>" \
-e WORKER_NAME="docker-mining" \
ghcr.io/lpmatos/docker-crypto-miner:mainShows information logged of the running container:
docker logs -f crypto-mineror
docker logs --tail 1000 crypto-minerClick here to see available image tags.
This section aims to describe at a high level what the tools we use are and how we use them, without reproducing documentation that is better written (and more up to date) in the repositories and websites of these tools themselves. It's recommended to familiarize yourself with these tools as early as possible.
Basically XMRig is a free and open source mining program. It can be installed on Windows, Linux and macOS, and allows you to mine the RandomX algorithm. Here is a brief example of the run command:
xmrig.exe -o rx.unmineable.com:3333 -a rx -k -u COIN:YOUR_ADDRESS.WORKER_NAME#REFERRAL_CODE -p x pause- COIN: it's the coin that you're extracting, for example: ADA, TRX, WIN or more. Also, keep the
:symbol between the currency and your address. - YOUR_ADDRESS: must be a valid address for the currency you choose, otherwise the pool will return an error, also be sure to check the supported network for some currencies like TRC20 for USDT mining (TRON address).
- WORKER_NAME: it's any name that you would like to define for your worker.
- REFERRAL_CODE: it's the parameter used to reduce the mining rate.
The unmineable is a mining pool that enables anyone to become a miner using a personal computer.
The acronym ASIC describes a series of computer equipment designed from start to finish to deliver maximum performance in cryptocurrency mining tasks.
RandomX is a proof-of-work (PoW) algorithm that is optimized for general-purpose CPUs. RandomX uses random code execution (hence the name) together with several memory-hard techniques to minimize the efficiency advantage of specialized hardware.
A mining rig is a mining platform. The platform could be a dedicated miner where it was purchased, built and operated specifically for mining, or it could be a computer that meets other needs, such as a gaming system, and is used to mine only on a part-time.
The cpulimit is a tool that allow us to limit CPU usage per process. It gives us some ways to identify the desired process, either by process name, PID or executable path. It's useful for controlling batch jobs when you don't want them eat too many CPU cycles. The purpose is to prevent a process from running for more than a specified proportion of time. In addition, it's also able to adapt to the overall system load dynamically and quickly.
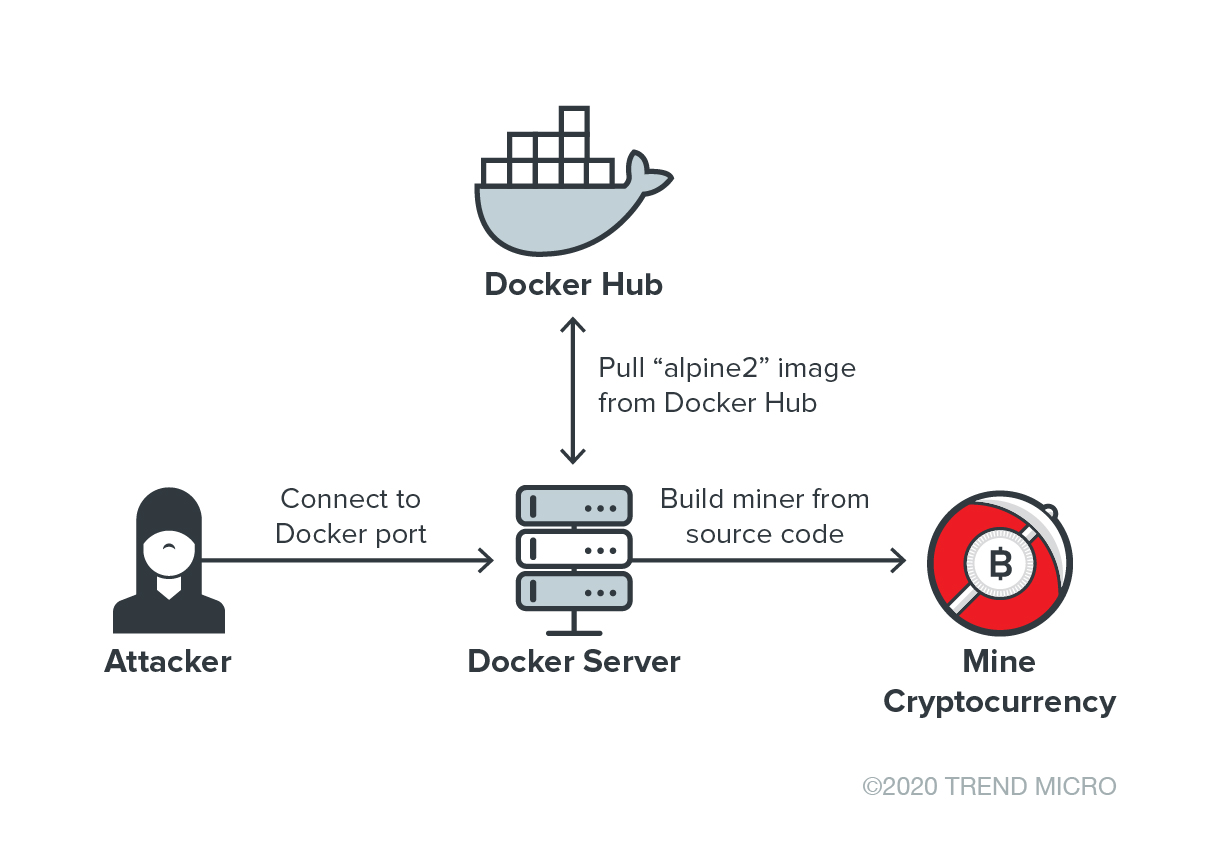
Pay attention to the images that you use for these purposes and protect yourself from cryptojacking. Containers have become frequent targets of threat actors who conduct malicious cryptocurrency mining and other attacks. Last year, Trend Micro came across activities of cryptocurrency miners that were deployed as rogue containers using a community-distributed image published on Docker Hub. In May, researchers found an open directory containing a malicious cryptocurrency miner and Distributed Denial of Service (DDoS) bot that targeted open Docker daemon ports. In the attack, an Alpine Linux container was created to host the cryptocurrency miner and DDoS bot.
- Thanks @rundqvist for sharing your project.
👤 Hey!! If you like this project or if you find some bugs feel free to contact me in my channels:
- Linktree: https://linktr.ee/lpmatos
To check the change history, please access the CHANGELOG.md file.
Currently the project is being maintained and constantly changing with new features. 👾
Please consider donating to the xmrig team, and if you find this docker image useful, donations for work on dockerizing the build and mining app are appreciated at any of the folllowing addresses: